If you are a user of one of the following products/features and would like to know which SFTP Ciphers/Encryption Algorithms are supported, please check the table below.
- SSIS PowerPack
- Secure FTP Connection Manager
- ODBC Power Pack
- ZappySys SFTP CSV Driver
- ZappySys SFTP JSON Driver
- ZappySys SFTP XML Driver
- Data Gateway Connector
- Native - ZappySys SFTP CSV
- Native - ZappySys SFTP JSON
- Native - ZappySys SFTP XML
List last updated on 10/30/2025
The ciphers/Encryption list on this page assumes you have at least the following versions. If you are running an older version, then you may not have some ciphers/encryption algorithms supported.
- For SSIS PowerPack
- Version 5.8.0 or Higher [Released on Oct 16, 2025 or later]
- For ODBC PowerPack
- Version 2.2.0 or Higher [Released on Oct 16, 2025 or later]
SSH ciphers
ZappySys SFTP’s SSH module supports a number of security algorithms:
-
Encryption algorithms (AES, AES/GCM, ChaCha20/Poly1305, Triple DES, Twofish, Blowfish, RC4).
-
Encryption modes (CBC, CTR, AEAD).
-
Host key algorithms (RSA, DSS, ECDSA, EdDSA).
-
Key exchange algorithms (Diffie-Hellman or Elliptic Curve Diffie-Hellman).
-
MAC algorithms (SHA-2, SHA-1, MD5).
How to change SFTP Key Exchange, Mac, Encryption, and Host Key Algorithms
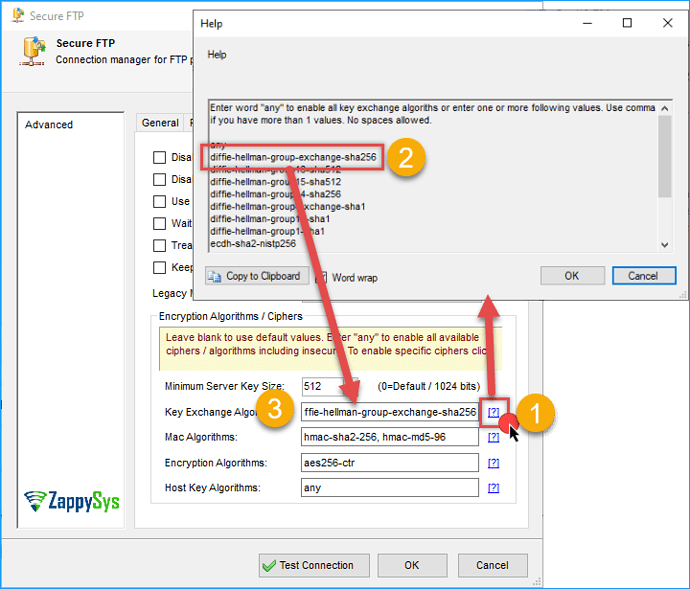
In most cases, you won’t ever have to specify Ciphers / Encryption Algorithms manually. However, if you have to, follow these steps. For SSIS-specific steps, check this article.
- For ODBC / SSIS Open SFTP Connection
- Go to SFTP Settings Tab
- Enter valid value(s) in the following fields.
Key exchange ciphers
Use Key Exchange Algorithms property to enable/disable whole categories of key exchange ciphers. The following table lists supported key exchange ciphers:
| Cipher ID | Key length | Description | Note |
|---|---|---|---|
| diffie-hellman-group-exchange-sha256 | Negotiated | Diffie Hellman with group exchange and SHA-256 hash | Available on all* platforms. |
| diffie-hellman-group16-sha512 | 4096 bits | Diffie Hellman with Oakley Group 16 and SHA-512 hash | Available on all* platforms. |
| diffie-hellman-group15-sha512 | 3072 bits | Diffie Hellman with Oakley Group 15 and SHA-512 hash | Available on all* platforms. |
| diffie-hellman-group14-sha256 | 2048 bits | Diffie Hellman with Oakley Group 14 and SHA-256 hash | Available on all* platforms. |
| diffie-hellman-group-exchange-sha1 | Negotiated | Diffie Hellman with group exchange and SHA-1 hash | Available on all* platforms. |
| diffie-hellman-group14-sha1 | 2048 bits | Diffie Hellman with Oakley Group 14 and SHA-1 hash | Available on all* platforms. |
| diffie-hellman-group1-sha1 | 1024 bits | Diffie Hellman with Oakley Group 2 and SHA-1 hash | Available on all platforms. Insecure. Disabled by default. |
| ecdh-sha2-nistp256 | 256 bits | Elliptic Curve Diffie Hellman with NIST P-256 curve and SHA-256 hash | Available on Windows 10/11, Windows Server 2016/2019/2022 and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| ecdh-sha2-nistp384 | 384 bits | Elliptic Curve Diffie Hellman with NIST P-384 curve and SHA-384 hash | Available on Windows 10/11, Windows Server 2016/2019/2022 and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| Disabled by default. | |||
| ecdh-sha2-nistp521 | 521 bits | Elliptic Curve Diffie Hellman with NIST P-521 curve and SHA-512 hash | Available on Windows 10/11, Windows Server 2016/2019/2022 and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| Disabled by default. | |||
| ecdh-sha2-1.3.132.0.10 | 256 bits | Elliptic Curve Diffie Hellman with secp256k1 curve and SHA-256 hash | Available on Windows 10/11 and Windows Server 2016/2019/2022. |
| Disabled by default. | |||
| curve25519-sha256 | |||
| (curve25519-sha256@libssh.org) | 256 bits | Elliptic Curve Diffie-Hellman on Curve25519 with SHA-256 hash | Available on Windows 10/11 and Windows Server 2016/2019/2022. External plugin needed for other platforms. |
Host key algorithms
Set Host Key Algorithms property to enable/disable whole categories of host key algorithms. The following table lists supported host key algorithms:
| Algorithm ID | Description | Note |
|---|---|---|
| rsa-sha2-256 | RSA with SHA-256 hash | Available on all platforms. |
| rsa-sha2-512 | RSA with SHA-512 hash | Available on all platforms. |
| ssh-dss | NIST Digital Signature Algorithm (DSA) with SHA-1 hash | Available on all platforms. |
| ssh-rsa | RSA with SHA-1 hash | Available on all platforms. |
| ssh-rsa-sha256@ssh.com | RSA with SHA-256 hash | Available on all platforms. |
| x509v3-rsa2048-sha256 | X.509 certificate with RSA (2048-bit or larger key) and SHA-256 hash | Available on all platforms. |
| x509v3-sign-rsa-sha256@ssh.com | X.509 certificate with RSA and SHA-256 hash | Available on all platforms. |
| x509v3-sign-rsa | X.509 certificate with RSA and SHA-1 hash | Available on all platforms. |
| x509v3-sign-dss | X.509 certificate with DSA and SHA-1 hash | Available on all platforms. |
| ssh-ed25519 | Ed25519, an Edwards-curve Digital Signature Algorithm (EdDSA) | Available on all platforms. |
| ecdsa-sha2-nistp256 | Elliptic Curve Digital Signature Algorithm (ECDSA) on NIST P-256 curve with SHA-256 hash | Available on Windows** and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| ecdsa-sha2-nistp384 | Elliptic Curve Digital Signature Algorithm (ECDSA) on NIST P-384 curve with SHA-384 hash | Available on Windows** and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| Disabled by default. | ||
| ecdsa-sha2-nistp521 | Elliptic Curve Digital Signature Algorithm (ECDSA) on NIST P-521 curve with SHA-512 hash | Available on Windows** and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| Disabled by default. | ||
| ecdsa-sha2-1.3.132.0.10 | Elliptic Curve Digital Signature Algorithm (ECDSA) on secp256k1 curve with SHA-256 hash | Available on Windows 10/11 and Windows Server 2016/2019/2022. |
| Disabled by default. | ||
| x509v3-ecdsa-sha2-nistp256 | X.509 certificate with Elliptic Curve Digital Signature Algorithm (ECDSA) on NIST P-256 curve with SHA-256 hash | Available on Windows** and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| x509v3-ecdsa-sha2-nistp384 | X.509 certificate with Elliptic Curve Digital Signature Algorithm (ECDSA) on NIST P-384 curve with SHA-384 hash | Available on Windows** and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| Disabled by default. | ||
| x509v3-ecdsa-sha2-nistp521 | X.509 certificate with Elliptic Curve Digital Signature Algorithm (ECDSA) on NIST P-521 curve with SHA-512 hash | Available on Windows** and on Linux with .NET Core 2.1 or later. External plugin needed for other platforms. |
| Disabled by default. |
Encryption ciphers
Set Encryption Algorithms property to enable/disable whole categories of encryption ciphers. The following table lists supported encryption ciphers:
| Cipher ID | Description | Note |
|---|---|---|
| aes256-gcm@openssh.com | AES in GCM mode with 256-bit key | |
| aes128-gcm@openssh.com | AES in GCM mode with 128-bit key | |
| chacha20-poly1305@openssh.com | ChaCha20/Poly1305 AEAD cipher with 256-bit key | |
| aes256-ctr | AES in CTR mode with 256-bit key | |
| aes192-ctr | AES in CTR mode with 192-bit key | |
| aes128-ctr | AES in CTR mode with 128-bit key | |
| aes256-cbc | AES in CBC mode with 256-bit key | |
| aes192-cbc | AES in CBC mode with 192-bit key | |
| aes128-cbc | AES in CBC mode with 128-bit key | |
| 3des-ctr | TripleDES in CTR mode | |
| 3des-cbc | TripleDES in CBC mode | |
| twofish256-ctr | Twofish in CTR mode with 256-bit key | |
| twofish192-ctr | Twofish in CTR mode with 192-bit key | |
| twofish128-ctr | Twofish in CTR mode with 128-bit key | |
| twofish256-cbc | Twofish in CBC mode with 256-bit key | |
| twofish192-cbc | Twofish in CBC mode with 192-bit key | |
| twofish128-cbc | Twofish in CBC mode with 128-bit key | |
| twofish-cbc | Twofish in CBC mode with 256-bit key | |
| blowfish-ctr | Twofish in CTR mode with 256-bit key | Disabled by default. |
| blowfish-cbc | Blowfish in CBC mode with 128-bit key | Disabled by default. |
| arcfour256 | ArcFour (RC4) stream cipher (with discard step) with 256-bit key | Disabled by default. |
| arcfour128 | ArcFour (RC4) stream cipher (with discard step) with 128-bit key | Disabled by default. |
| arcfour | ArcFour (RC4) stream cipher with 128-bit key | Disabled by default. |
MAC ciphers
Set Mac Algorithms property to enable/disable whole categories of message authentication code (MAC) ciphers. The following table lists supported MAC ciphers:
| Cipher ID | Description | Note |
|---|---|---|
| hmac-sha2-256-etm@openssh.com | SHA-256 (ETM mode) | |
| hmac-sha2-256 | SHA-256 | |
| hmac-sha2-512-etm@openssh.com | SHA-512 (ETM mode) | |
| hmac-sha2-512 | SHA-512 | |
| hmac-sha1 | SHA-1 | |
| hmac-md5 | MD5 | Disabled by default. |
| hmac-sha1-96 | SHA-1 (trimmed to 96 bits) | Disabled by default. |
| hmac-md5-96 | MD5 (trimmed to 96 bits) | Disabled by default. |