Introduction
This article will show you how to use Wireshark, a popular open-source network protocol analyzer. It is used for network troubleshooting, analysis, software, communications protocol development, and education. Wireshark allows users to capture and interactively browse the traffic on a computer network in real time.
Prerequisites
- Install Wireshark: Download and install Wireshark from the official website.
- Download ZappySys SSIS PowerPack
- Install Visual Studio 2022
Steps
-
Launch Wireshark after installation. To capture network traffic, you may need to run it as an administrator on Windows.
-
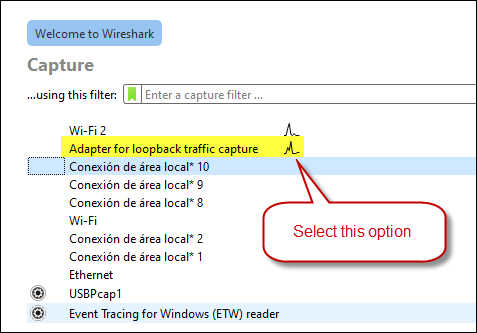
Go to the “Capture” menu and select “Interfaces” to choose the network interface from which you want to capture traffic (e.g., Ethernet, Wi-Fi). We used: Adapter for loopback traffic capture
-
Click the selected network interface and click the “Start” button to capture traffic.
-
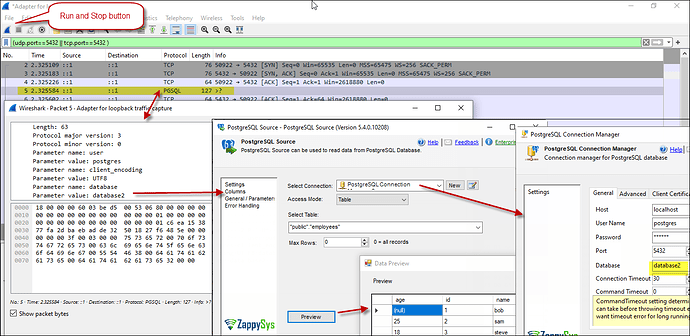
Once you have captured enough traffic or completed your tests, click the “Stop” button in Wireshark to stop capturing.
-
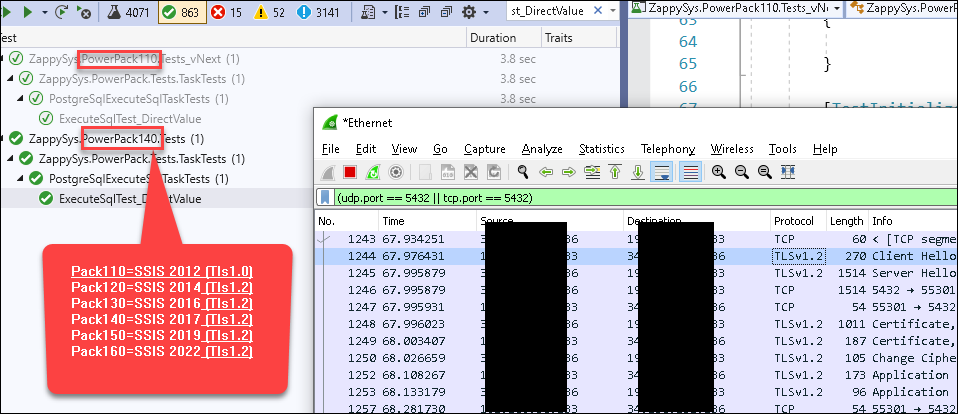
Wireshark’s main window displays captured packets. You can apply filters, search for specific packets, and analyze PostgreSQL-related packets. e.g., using the filter
pgsqlor(udp.port==5432 || tcp.port==5432 ). -
You can apply a capture filter to capture only MySQL traffic. MySQL typically uses port 3306, so you can apply a filter like
tcp.port==3306. -
For the TLS option, you need to check the protocol column:
-
If applicable, Click on individual packets to view their details, including the PostgreSQL protocol data.
-
You can save the captured packets for later analysis or export them in various formats (e.g., pcap, CSV) using the “File” menu.
Conclusion
Following these steps, you can use Wireshark to monitor and analyze SSL/TLS/Postgresql/MySq and other network traffic. However, capturing network traffic may require appropriate system permissions and configurations.
.